Analyzing the dump
Now that you have dumped the 128 blocks of 1MB – its time to re assemble it and start analyzing it.
cat *.bin > nand.binFavorite tool to start with… binwalk ! The output is not very verbose, but indicates that the NAND flash uses the UBI filesystem – which is common for NAND on embedded devices.
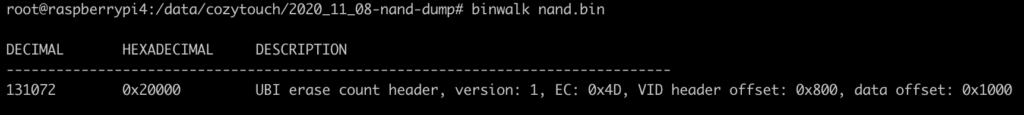
If we want to be able to work with the NAND image – and list and mount partition, one option is to emulate on our linux an MTD device. The various parameter describe flash size, block size, etc.
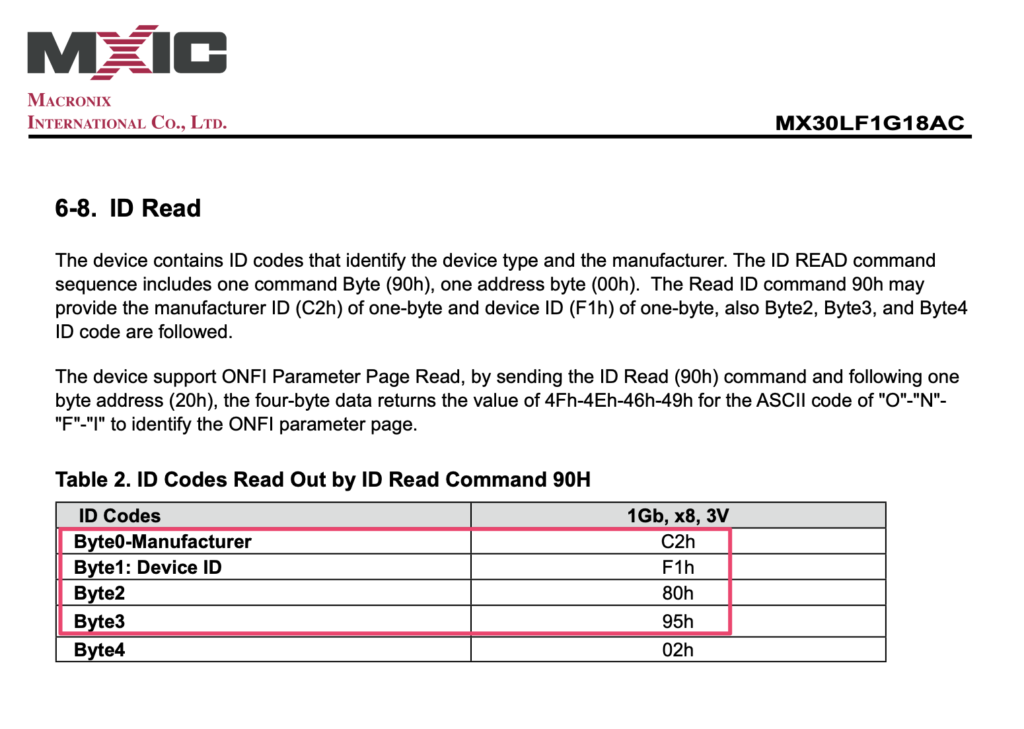
modprobe nandsim first_id_byte=0xc2 second_id_byte=0xf1 third_id_byte=0x80 fourth_id_byte=0x95The parameters values are directly taken from the Macronix documentation – to emulate the exact NAND device:
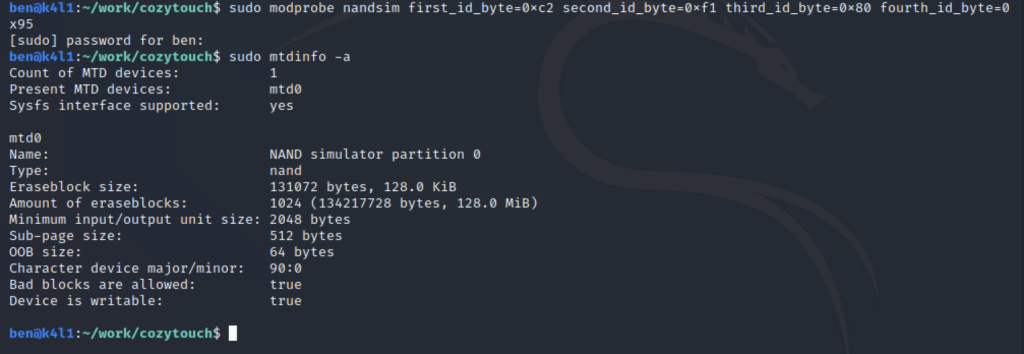
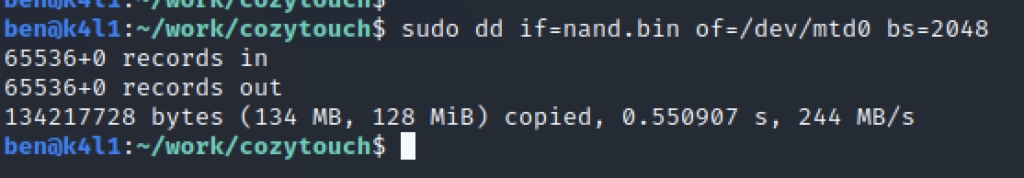
Now that the virtual NAND flash is created, just copy the content of the dump on it:
Enable the UBIFS, indicate that it’s on mtd0, and the block size is 2048:
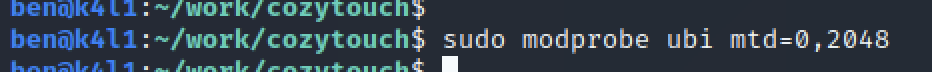
And – tadaaaa:
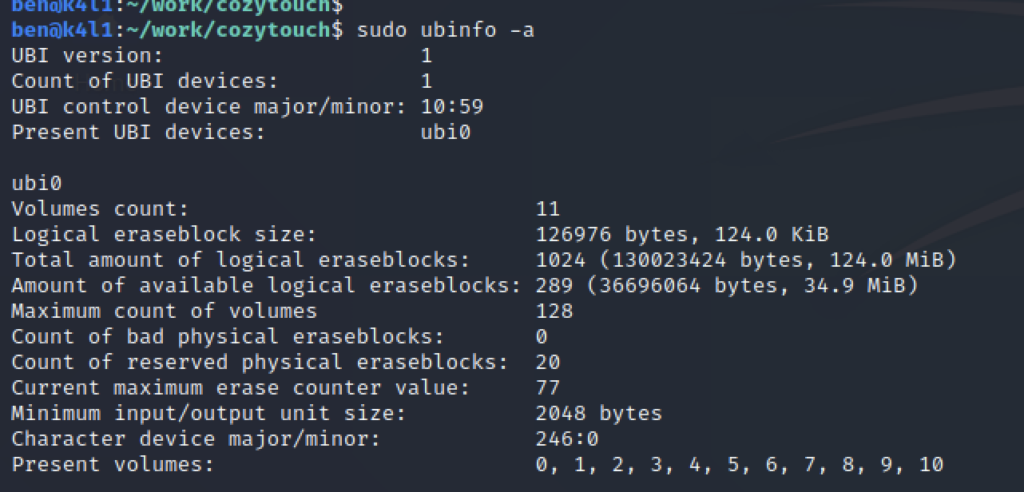
The full filesystem is composed of 11 volumes:
| Volume ID | Size (bytes) | Name |
| 0 | 25 197 | dtb |
| 1 | 25 197 | dtb-spare |
| 2 | 4 893 365 | kboot |
| 3 | 4 893 365 | kboot-spare |
| 4 | 8 192 | security |
| 5 | 8 192 | security-spare |
| 6 | 3 174 400 | persistent |
| 7 | 26 411 008 | root |
| 8 | 23 871 488 | apps |
| 9 | 26 284 032 | rootB |
| 10 | 126 976 | persistent-spare |
The device has some redundancy/failover in place to prevent a corrupted storage/partition and seems to have self-restore facility (-spare volumes).
You can find the filesystem / data type using binwalk on each UBI volume, for example:
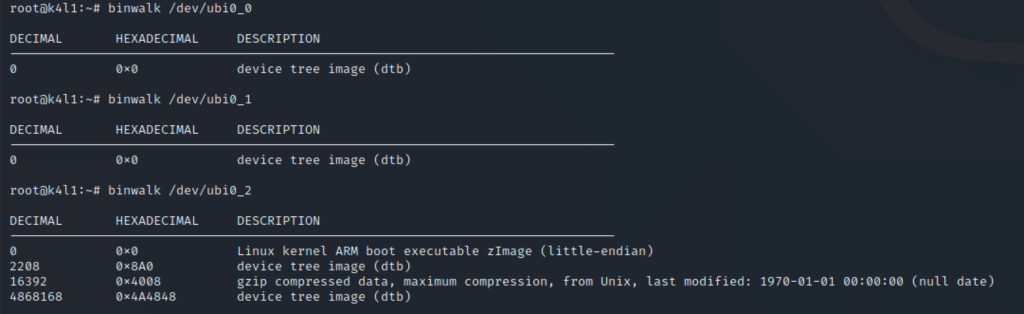
DTB (device tree binding) is used by the kernel to describe the hardware, and determine modules/drivers to be loaded. We’ll not be touching at it.
There is next KBOOT – which is the device specific bootloader.
Finally, we are interested in the following volumes (not mentioning the spare one):
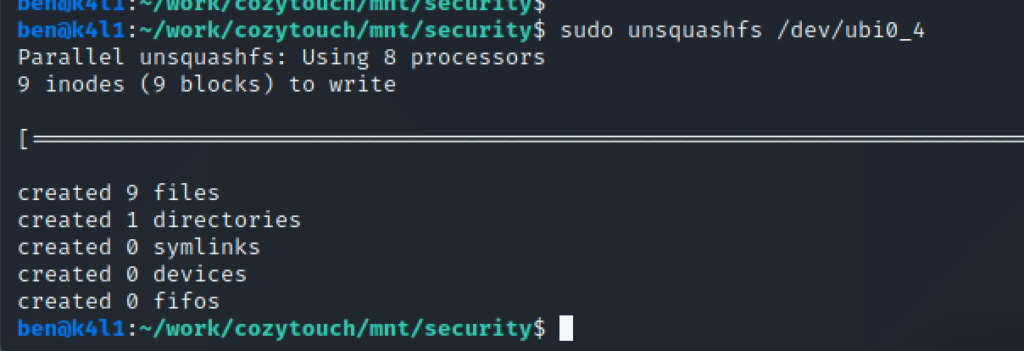
– security : SquashFS
– persistent : UbiFS
– root : UbiFS
– apps : UbiFS
UbiFS partitions can be mounted straightforward – whereas the SquashFS needs to be extracted.
Now, mount each filesystem:
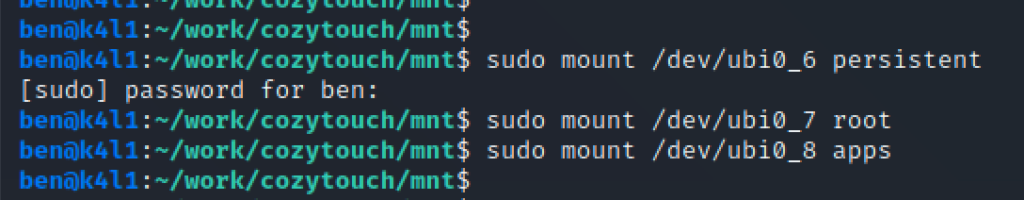
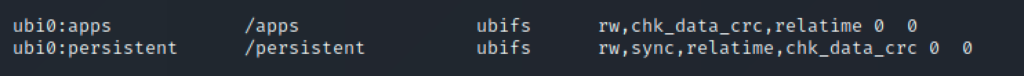
At this stage, you can start exploring the device file systems, and understand the logic. Looking at /etc/fstab from the root partition indicates that apps and persistent partitions are mounted in /apps and /persistent respectively:
By default, all the ports are closed on the device. What we want to do is be able to connect to the device first. What about enabling SSH ? read it in the next part !
